6. 测试平台
6.1. 测试用例
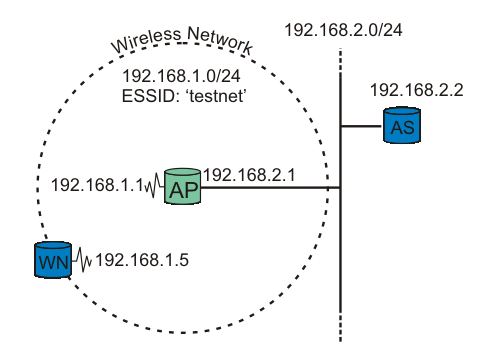
图示 测试平台:无线节点请求身份验证。
我们的测试平台由两个节点和一个接入点 (AP) 组成。一个节点充当 Supplicant (WN),另一个节点充当运行 RADIUS (AS) 的后端身份验证服务器。接入点是 Authenticator。有关说明,请参见图 测试平台。
 | 接入点能够到达(ping 通)身份验证服务器,反之亦然,这一点至关重要! |
6.2. 运行一些测试
运行一些测试
RADIUS 服务器在调试模式下启动。这将产生大量调试信息。重要的代码片段如下
radius 服务器现在已准备好处理请求!
上面包含了最有趣的输出。如果您收到任何错误消息而不是最后一行,请仔细检查配置(如上所述)。
现在 Supplicant 已准备好进行身份验证。在调试模式下启动 Xsupplicant。请注意,我们将看到两个启动脚本产生的输出startup.sh和startup2.sh.
# xsupplicant -c /usr/local/etc/1x/1x.conf -i eth0 -d 6 Starting /etc/1x/startup.sh Finished /etc/1x/startup.sh Starting /etc/1x/startup2.sh Finished /etc/1x/startup2.sh
同时,RADIUS 服务器正在产生大量输出。关键代码片段如下所示
Authenticator(接入点)也可能在其日志中显示如下内容
00:02:16 (Info): Station 0002a56fa08a Associated 00:02:17 (Info): Station=0002a56fa08a User="testuser" EAP-Authenticated
就是这样!Supplicant 现在已通过身份验证可以使用接入点!




